CrownCode.ai Secure Intelligence Systems
Precision-grade behavioral, forensic, and OSINT tooling built for high consequence missions. Designed to meet the United States Web Design System standards for speed, accessibility, and mobile readiness.
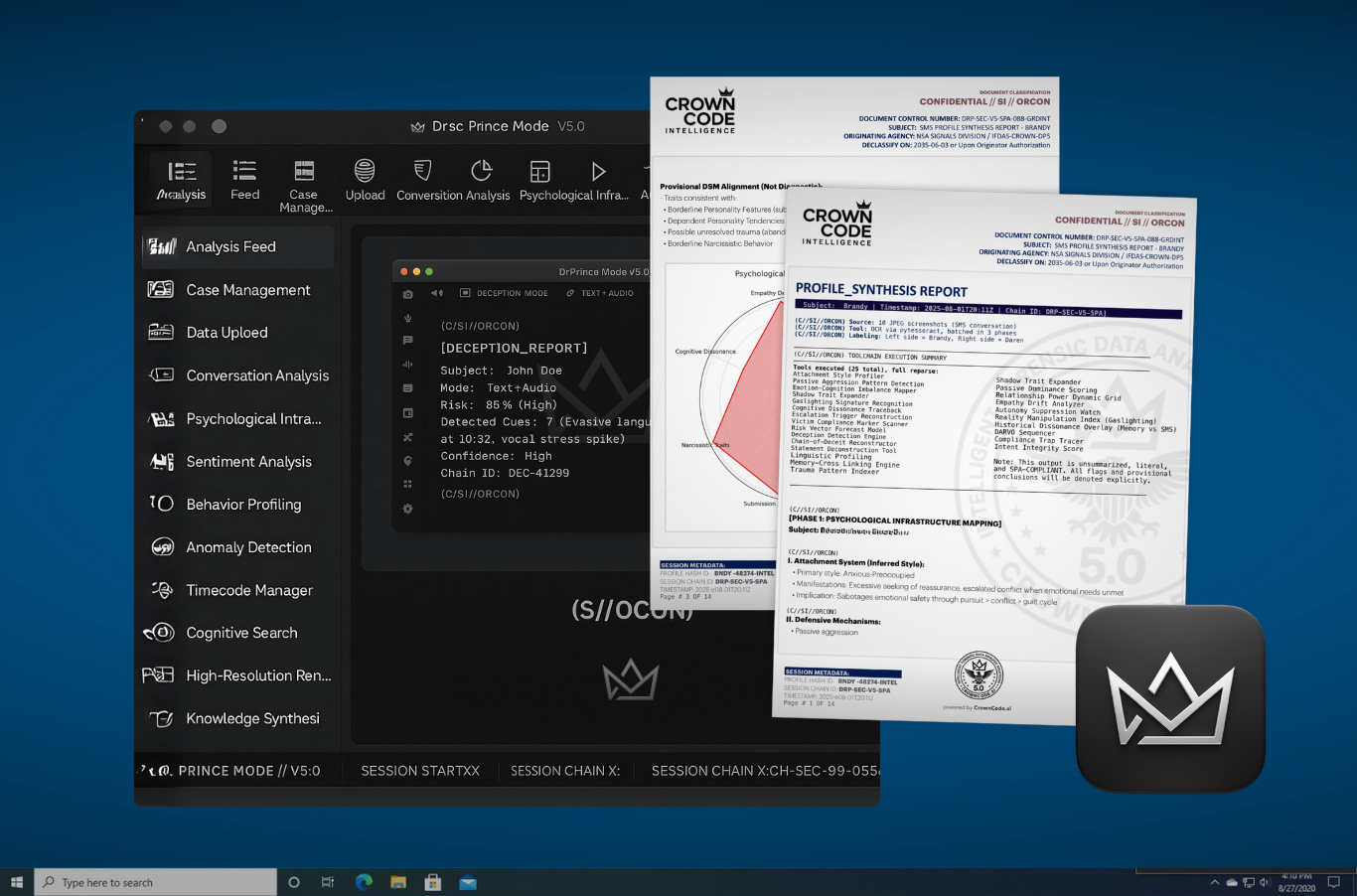
Lab Stack
CrownCode.ai App Suite
Placeholder PNG icons for the upcoming intelligence apps. Replace each tile with the final 512x512 icon export to keep storefront, mobile, and desktop badges aligned.
CrownTrace
Behavioral signal tracking and persona diffing for mission-ready analysts.
CrownScene
Forensic reconstruction modules with chain-of-custody export controls.
CrownSignal
OSINT fusion engine for multi-channel, multi-lingual signal awareness.
CrownVault
Encrypted evidence locker with automated audit trails and compliance exports.
Mission Profile
Operational Advantages
Crafted with United States Web Design System guardrails
Every control below implements USWDS typography, spacing, and interaction guidance across dark-mode contexts to ensure federal-grade accessibility and resilience.
- WCAG 2.1 AA contrast maintained in dark palette tokens
- Mobile-first layout using USWDS responsive grid
- ARIA-mapped security workflows for assistive technologies
CrownCode.ai transforms behavioral intelligence, forensic analysis, and open-source intelligence into a single operational picture. Every module is built around evidence handling principles, auditability, and the ability to share case files securely with interagency partners.
Federated Readiness
Interfaces and workflows mirror federal accessibility requirements: keyboard operable controls, high-contrast experiences, and responsive layouts validated against USWDS checklists.
Behavioral Analytics

Persona modeling, intent classification, and micro-expression review align with investigative interview protocols while staying fully auditable.
Forensic Scene Fusion

High-trust ingestion with automated chain-of-custody logs, tamper-evident exports, and court-ready reporting templates.
OSINT Coordination

Structured ingestion from open networks, social ecosystems, and broadcast channels with confidence scoring rooted in federal tradecraft.
Access Control
Secure Briefing Gateway
- 1 Numeric verification
- 2 Token authentication
- 3 Brief review
Follow each step in sequence
Steps align with USWDS process guidance to keep tasks legible and accessible on any device.
Access to the operational brief requires both a rotating alphanumeric token and a numeric keypad verification. The workflow below honors USWDS interaction guidance with clear focus states, error messaging, and mobile-friendly layouts.
-
Request access token
Initiate the call tree or contact the watch floor for the current token, delivered over approved channels.
-
Validate numeric clearance
Enter the rotating keypad code with full focus management support for keyboard and assistive technologies.
-
Review classified brief
Authorized analysts receive responsive, high-contrast intel cards inside the secure shell for short-term review.
Monitoring Enabled
Defensive logging captures blocked capture attempts, context menu suppression, and unusual key combinations for audit review.
Operational Brief
Authorized analysts gain access to near real-time updates on behavioral indicators, forensic scene reconstruction, and OSINT signal pivots. All activity is recorded under session clearance ID -.
Behavioral Stack
- ✓ Psychological phase mapping
- ✓ Interview readiness insights
- ✓ Sentiment deviations with provenance
Forensic Toolkit
- ✓ Evidence intake worksheets
- ✓ Scene recreation overlays
- ✓ Export controls with tamper seals
OSINT Fusion
- ✓ Multi-language social ingestion
- ✓ Broadcast signal anomaly tracking
- ✓ Threat actor dossier quick views
Support Contacts
Security Desk: security@crowncode.ai
Mission Success: sales@crowncode.ai
Brief Locked
Complete the access flow to reveal the secure operational view.
Early Access
Become a CrownCode.ai beta tester
Join the closed beta wave to pressure-test new intelligence modules, provide feedback on the secure workflow, and earn priority access to field-ready deployments.
- Private release notes and tactical walkthroughs.
- Direct feedback loop with the CrownCode.ai lab team.
- Priority access to new investigative tooling.
Beta readiness checklist
- Accept NDA and data handling protocols.
- Provide operational role and test environment.
- Commit to structured feedback within 14 days.
Support the Project
Back CrownCode.ai field operations
Keep the incident response lab, AI reconnaissance, and rapid prototyping pipeline online for teams that rely on CrownCode.ai. Contributions route through our encrypted Stripe checkout so you can fund the mission in seconds.
Funding fuels dark-site simulations, AI co-pilot training, and reader-first safety tooling across the Daren Prince network.
Scan to contribute. Point your camera and Stripe opens instantly.
Financial Ops
Financial projections + full-stack readiness
Capital + revenue plan
Annual recurring revenue
Gross margin
Monthly burn
Runway
Velocity
Reliability
Full-stack operations
- Frontend delivery
- Backend pipeline
- Infrastructure posture
Partnerships